Security?
Security Cameras, Access Controllers, Monitoring and more security features


Cameras
The IP Cameras technology offers many advantages over the standard coaxial technology. It enables the use of network cables which covers greater distances without the need for signal amplifiers. The quality of the image has a significantly higher resolution, it supports more Megapixels than Coax Cameras. Features include facial recognition, count of people entering and exiting the property and other advanced functionalities.

Access Controllers

User Access
We use several technologies to control the access to all resources in your business. One of then is Active Directory of Microsoft. A server running Active Directory Domain Services (AD DS) is called a domain controller. It authenticates and authorizes all users and computers in a Windows domain type network—assigning and enforcing security policies for all computers and installing or updating software. For instance, when a user logs into a computer that is part of a Windows domain, Active Directory checks the submitted password and determines whether the user is a system administrator or normal user. Also, it allows management and storage of information, provides authentication and authorization mechanisms, and establishes a framework to deploy other related services: Certificate Services, Federated Services, Lightweight Directory Services and Rights Management Services.

Monitoring System
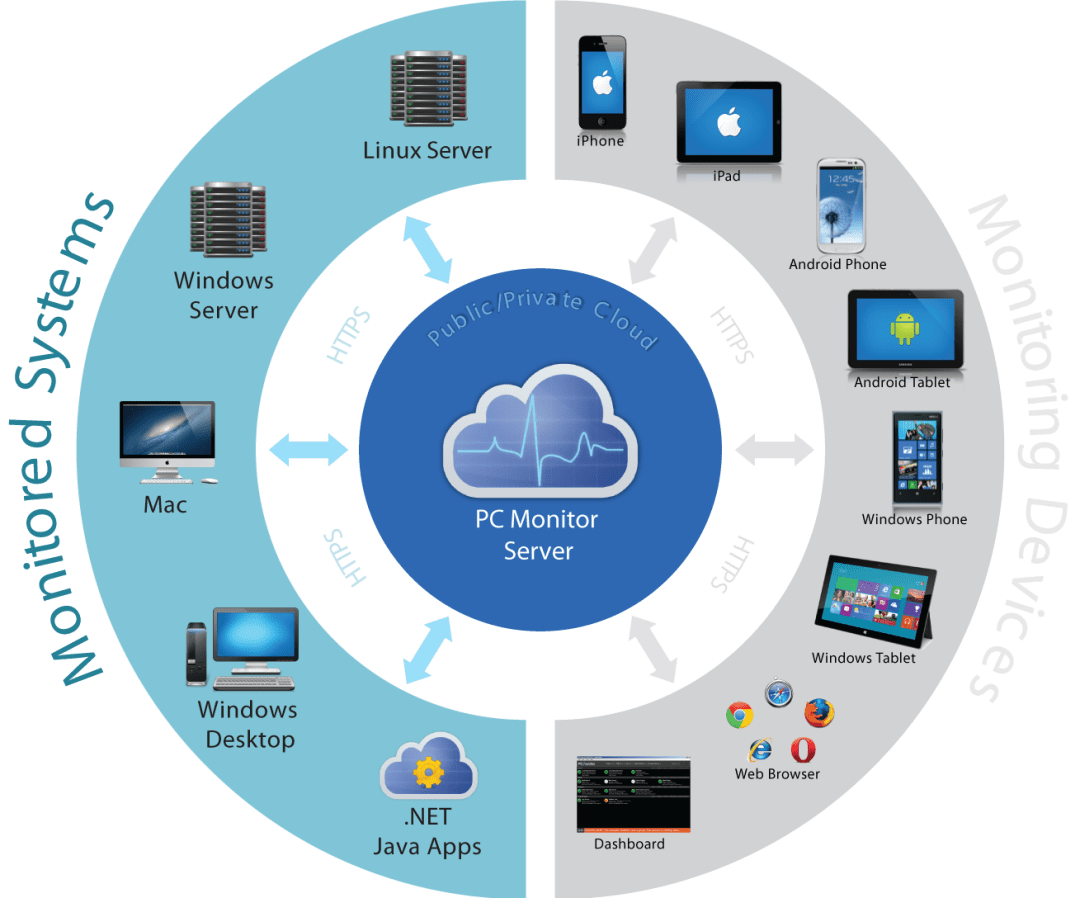
The use of this software is not visible to the employees. Only the business is in full charge. All member staff is under scrutinized monitoring at all times with Real Time monitoring.
Contact Us
040-48551063, 8801023888
#3-7-230, 3rd Floor, Munela Bhawan, Behind Parvathi Hospital, Vikrampuri Colony, Karkhana, Secunderabad-500009
Request A Quote
Our estimates are always free and our solutions are priceless!…Contact us now!
Our Clients










